Zero Trust is a security strategy that meets the complex safety needs of a modern work environment. This security setup is ideal for protecting a company that relies on cloud computing, remote workforces, and distributed systems.
This article teaches everything you need to know about the Zero Trust security model. We explain how Zero Trust works, what benefits it brings, and why this security strategy is the most effective way of protecting a modern enterprise.
What is the Zero Trust Model?
Zero Trust is a security strategy in which a company does not automatically trust anything inside or outside the network’s perimeter. Instead, the system verifies every user and device before granting access.
A Zero Trust approach enables a business to:
- Thoroughly check every access request.
- Protect data, applications, and networks from outside and inside dangers.
- Safely run and thrive in distributed systems.
- Establish an automatic cycle of scanning and responding to threats.
- Easily comply with FISMA, HIPAA, PCI, GDPR, CCPA, and similar data privacy and security laws.
The goal of Zero Trust is to protect the company from advanced cybersecurity threats and data breaches. Continuous verification of trust across every device, user, and application enables a company to stop:
- Phishing attacks targeting customers and workers.
- Lateral movement through the network.
- Hackers from using stolen user passwords and application database credentials.
- Database exfiltration via a compromised application host.
- Malicious elevation of application host privileges.
- Unprivileged access to a workstation.
Zero Trust may include continuous authentication concepts but is not a form of CA. Other terms for Zero Trust are Zero Trust Network and Zero Trust Architecture.
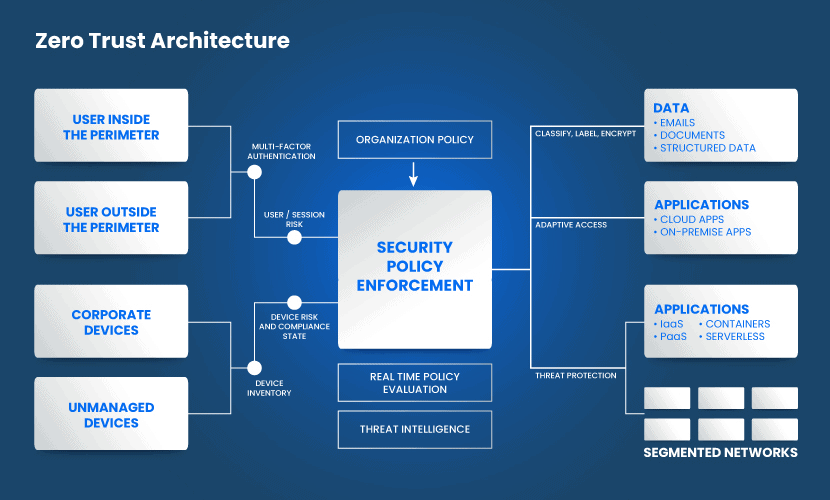
How the Zero Trust Model Works
Zero Trust checks every access request before allowing connection to any asset on the network. Security controls verify access rights based on attributes such as:
- User identity.
- Endpoint hardware types.
- Firmware versions.
- Operating system versions.
- Patch levels.
- Weak points and vulnerabilities.
- Installed applications.
- User logins.
Once security controls permit a user or a device to enter the network, the access is not indefinite. The system periodically verifies user identity to ensure constant protection of the system.
Zero Trust security policies tie directly to the workloads. Security stays as close to the assets as possible. The result is a protection system that travels with the workload and remains consistent in all environments.
Zero Trust does not only focus on prevention. If an attacker breaches the perimeter, exploits a bug, or bribes an insider, the hacker has limited access to valuable data. The system detects and responds to abnormal behavior before the attacker has enough time to do damage.
Zero Trust incorporates a range of principles and technologies to protect a system, including:
- Multifactor authentication.
- Identity and access management (IAM).
- System orchestration.
- Analytics.
- Encryption.
- File system permissions.
- Next-generation endpoint security technology.
Read about the best network security tools and see how they improve the safety of your organization.
Automation is a significant aspect of the Zero Trust model. Humans cannot keep up with the volume of monitoring events necessary to enforce Zero Trust on an enterprise level. Automation keeps security systems running and enforces policies 24/7.
Automate as many remediation, monitoring, and threat detection systems as possible. Such a strategy ensures optimal protection and frees up the team to work on more business-critical tasks.
Know the automated security testing best practices before you start removing manual tasks from your security processes.
Traditional Security Architecture vs. Zero Trust Architecture
Traditional network security relies on the castle-and-moat concept. Castle-and-moat security focuses on preventing access from outside the network while trusting every user and device already within the perimeter.
This security setup has several flaws that make it ineffective for today’s workloads:
- Companies no longer keep data in a single contained area but in large, distributed systems that often include cloud vendors.
- Trusting users and devices already within the network is no longer safe due to the mobile workforce, BYOD (Bring Your Own Device) policies, IoT, and cloud adoption.
- Once an attacker gains access to the network, nothing is stopping lateral movement through the system.
- Employees and customers access applications from a range of devices and locations.
The castle-and-moat concept is no longer capable of protecting an enterprise-level network. Zero Trust security, however, offers features ideal for modern corporate systems:
- The network does not trust any user or device by default.
- Verification is necessary for everyone trying to access resources both from inside and outside of the network.
- Every segment in a distributed system has individual security controls that prevent lateral movement.
What Does Zero Trust Security Protect?
Zero Trust is ideal for protecting modern business environments with a combination of public and private clouds, SaaS applications, and DevOps pipelines. The Zero Trust security model defends:
- Data: Zero Trust sets clear rules about where data lives, who can access it, and what is sensitive or stale.
- Networks: Zero Trust networks rely on segmentation, isolation, and strict restrictions to keep attackers out.
- People: Humans are typically the weakest link in any security strategy. Zero Trust security limits, monitors, and enforces how users access resources both inside and outside the network. As a result, threats such as phishing, bad passwords, or malicious insiders are less dangerous.
- Workloads: The Zero Trust model protects the entire stack of applications and back-end software. Strict controls protect everything from data storage, to the operating system and web front-end.
- Devices: Every connected device in a network is a potential entry point for attackers. Zero Trust security model isolates and protects every device in the infrastructure with separate controls.
Benefits of Zero Trust Security
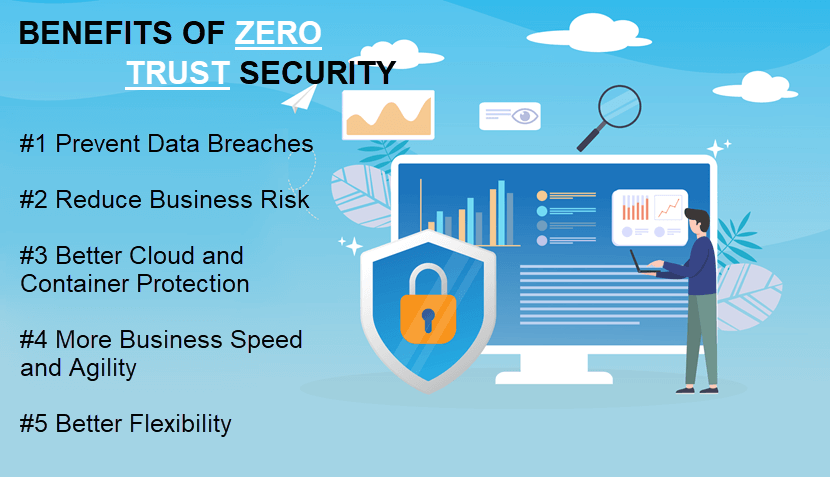
1. Data Breach Prevention
Data is the most common target of cyberattacks as hackers typically go after:
- Personally identifiable data (PII).
- Protected health information (PHI).
- Payment card information (PCI).
- Intellectual property (IP).
Zero Trust is the most effective method of protecting data in an enterprise-level network. Accessing information requires thorough verifying, so every piece of valuable data has a strong layer of protection.
2. Less Business Risk
The Zero Trust model is excellent at detecting suspicious behavior. All users, applications, and services are malicious and cannot communicate until the system verifies their identity. Zero Trust reduces risk by uncovering activity across the network and continuously analyzing how assets are communicating.
Apply cybersecurity best practices to your business and ensure the safety of your data and assets.
3. Cloud and Container Protection
The Zero Trust model provides both the visibility and control necessary to keep cloud and container environments safe. If a workload fails the verification, Zero Trust prevents it from communicating anywhere on the system.
Read more about cloud security and learn how to protect your on-cloud operations.
4. More Business Speed and Agility
Traditional security controls often slow down business operations. Blocked ports and shut down hosts prevent employees from reaching data, cause errors across the system, and slow down processes.
A Zero Trust model does not rely on static network constructs that slow the system down. Protection follows the workload instead of operating from a security checkpoint. Blocks and shutdowns occur in isolation and do not impact other parts of the system.
Zero Trust also provides a clear overview of all users, devices, data, servers, applications, and containers in the infrastructure.
5. Better Flexibility When Moving Network Assets
Teams often move applications, data, and IT services across the infrastructure. Before the Zero Trust model, moving assets between environments required the team to recreate security policies at the new location manually.
Zero Trust eliminates this time-consuming and error-prone process. The team centrally manages application and data security policies, while automation tools migrate policies on-demand.
Principles of the Zero Trust Security Model
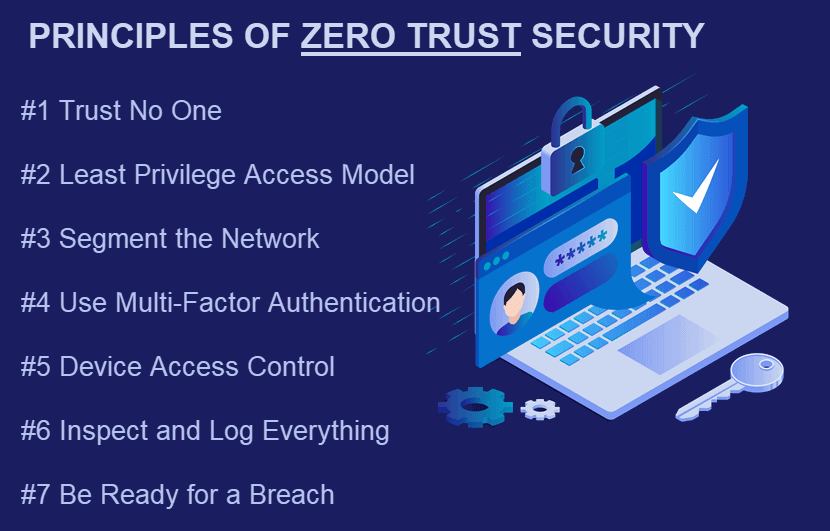
1. Trust No One
The core concept behind Zero Trust is that there are attackers both within and outside the network. The system should never automatically trust users or devices, so every access attempt is a threat until a verification confirms otherwise.
User re-authentication is a vital rule of Zero Trust. Each time a user accesses the system, security controls should reverify the right to access the resource.
2. Use the Least Privilege Access Model
Restrict users to only as much access as they require to perform their duties. Limited access minimizes each user’s exposure to sensitive parts of the network and lowers the attack surface. A single compromised account does not enable an attacker to access large amounts of data.
3. Segment the Network
Network segmentation is the practice of breaking up a network into small zones with separate security controls. A user or program with access to one zone does not have the right to access another area without separate authorization.
Segmentation enables the use of strict access control policies that protect individual workloads. If a breach occurs, network segmentation limits lateral movement and improves system resilience.
4. Multi-Factor Authentication (MFA)
MFA asks users to provide more than one piece of evidence to verify their identity. A typical application of MFA is the 2-factor authorization (2FA). With 2FA, a user must type in a password and enter a code sent to another device.
MFA is a must for any Zero Trust security scheme as it limits brute force attacks.
5. Device Access Control
Zero Trust requires strict controls on device access. The system must:
- Monitor the number of different devices trying to access the network.
- Verify every access attempt.
Strict device access control further reduces the attack surface of the network.
6. Monitor and Log Everything
Continuous inspection of users, devices, and activities is essential to Zero Trust. A company should use an automation tool to monitor every network call, file access, and email for malicious activity.
Monitoring and logging help quickly identify:
- Signs of data breaches.
- Dangerous user accounts.
- Patterns in malicious behavior.
- System weak points.
- Ransomware attacks.
Real-time monitoring also limits breakout time, the critical window between when attackers access the first machine and when they start moving laterally to other systems.
Read about the 17 cyberattack types that hold the most danger to businesses in 2021.
7. Be Ready for a Breach
Data breaches are inevitable, even in a Zero Trust environment. Prepare for an attack by:
- Minimizing blast radius.
- Limiting lateral movement in the network.
- Preparing a data backup strategy.
- Setting response tactics.
Ensure your business is ready for an attack with our Cyber Security Incident Response Plan (CSIRP) checklist.
Grow Your Business Without Costly Setbacks
Zero Trust is the most effective method of protecting large networks from advanced cyber threats. This security model builds barriers around each asset and continually scans for dangers, allowing companies to grow without worrying about costly data breaches.
If you are looking for a safe Cloud solution that adheres to the most strict compliance policies, learn more about Data Security Cloud.



